Detecting stealthy Android malware
If you stay up to date with this blog you may have noticed I haven't made a new post in a while (about four months to be precise). There is a reason for this, and it's not just that I'm getting lazy. I've been working on a Master of Science degree at WPI, and my thesis project has been consuming all my free time. Now that I'm approaching the end of the project and the submission of my thesis paper I can write a bit about what I've been working on.
The problem
Current corporate network administration tools have too little insight into the connections made by employee-owned smartphones, especially in "Bring Your Own Device" (BYOD) scenarios that are becoming increasingly common. It is difficult for large organizations to maintain security across their networks with such little knowledge about—and control over—these mobile devices. The fact that these devices enter and exit the corporate network and connect to other networks, such as their cellular data provider's, on a daily basis complicates this issue. Smartphones have a wide range of powerful networking and computational abilities, and are typically privately owned by employees, which raises further concerns when integrating them into secure network environments.
For example, smartphones have been targeted by malware specifically designed to infiltrate corporate networks,1 such as "Dresscode," which disguises itself as a legitimate app in order to steal data and add infected devices to a botnet.2 The "xHelper" malware can automatically download and install arbitrary software specified by an attacker, and persists even after a factory reset.3 A black market malware-as-a-service model called Black Rose Lucy even offers control of infected Android devices to paying customers, potentially giving any malicious actor an entry point to a secure network.4
If mobile devices are to have access to sensitive corporate networks, administrators need new tools to monitor and control their network connections. These tools need to be powerful enough to detect when network connections are made by Trojan horse malware that is disguised as a benign app, while being still being easy to deploy and manage. For example, some existing solutions require recompiling Android’s kernel or gaining root access to their device, which is impractical for most users and exposes them to additional security risks.5
How we solve it
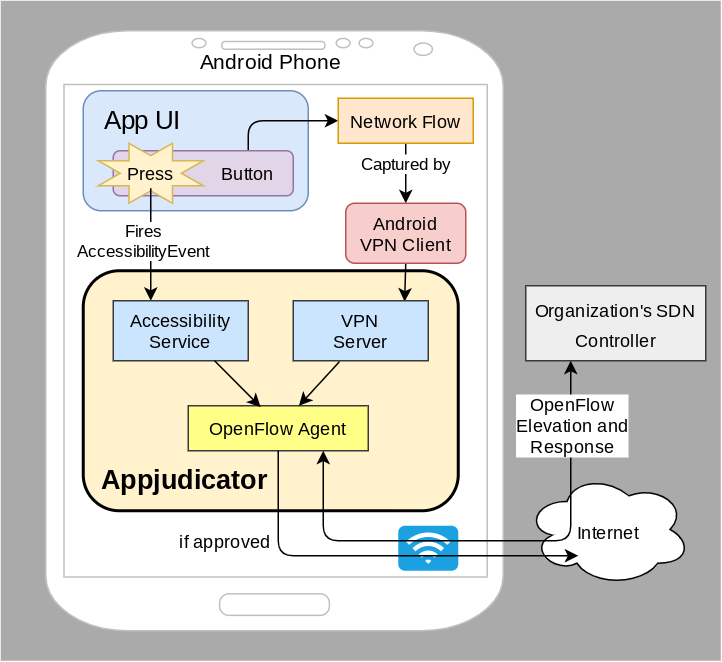
To solve these issues on Android devices, we propose a new app called which leverages user interface (UI) interaction and software defined networking (SDN) principles to determine whether network flows are legitimately user-initiated. The app has two components: an accessibility service that monitors UI interaction, and a VPN service that intercepts network flows and acts as an OpenFlow agent. We use these two sources of information to correlate network flows with user interaction in a way that is difficult for malware to evade, since it cannot physically interact with hardware input devices.
The UI monitoring component will use Android's accessibility API to asynchronously record user actions. This gives administrators the ability to accurately distinguish between human-driven and automated network requests. Meanwhile, the VPN service acts as an OpenFlow agent and rule cache, giving administrators fine-grained control over which connections the device is allowed to make. Flows are augmented with context from the specific device and application, and can be elevated to the organization's SDN controller if necessary.
Benefit over cost
Our application provides organizations with a new set of powerful, easy to use tools for monitoring BYOD Android smartphones in a simple app package that is easy for users to install. It does not require rooting, recompiling the kernel, or any other cumbersome processes. It can distinguish between user-generated and automated network requests with a high degree of confidence using techniques that are difficult for malware to evade. This makes users safer by detecting stealthy malware on their devices, and improves the organizations network security.
The costs of our system include the resource overhead of running the app (CPU cycles, battery power, etc.) and the cost of installing, running, and maintaining the controller server. We expect these costs to be a relatively small addition to existing resources. The app's UI monitoring and VPN service will also add some amount of latency to actions performed on the phone, but from experience developing a similar application for Microsoft Windows, called Harbinger, we expect this latency to be within acceptable levels.6 Harbinger introduced a maximum of six milliseconds of latency for 96% of network flows. For context, less than 16 milliseconds is undetectable on a standard 60 Hz display.
Prior work
Some aspects of this project have been studied by others before, but combines these aspects in new and important ways. Using a smartphone as an SDN agent has been investigated by Hanguard,7 and using UI interaction as context for identifying malicious app behavior was examined in AppIntent,8 but our system combines these approaches to form a novel solution for a distinct use case. One key difference is that AppIntent uses machine learning to conduct static analysis of apps, while enables live monitoring and response to malicious network flows in real time.
The combination of UI monitoring and SDN has been implemented on Microsoft Windows by Harbinger,6 and Kwon et al.,9 but we solve new challenges presented by the Android platform. For example, we are constrained by Android's rigid permissions system, we do not have root access to the device, and we cannot modify the kernel. These restrictions require novel techniques and systems.
Our work will focus on exploring the following research question:
Can UI interaction and network activity be used to successfully predict and associate network flows with user actions on Android devices with acceptable overhead?
To investigate we will perform a study with several popular Google Play apps to determine whether can successfully detect and block suspicious non-user-initiated network requests. We will also measure the total round-trip-time of network requests with the system enabled and disabled to determine the total latency it adds.
This is just a basic outline of my goals and approach to the project. In the coming weeks I expect to post a bit more about the specific implementation details, so stay tuned for that.
References
- Kan, Michael. 2016. "Android Malware That Can Infiltrate Corporate Networks Is Spreading." https://www.computerworld.com/article/3126390/android-malware-that-can-infiltrate-corporate-networks-is-spreading.html.
- Palmer, Danny. 2016. "Over 400 Instances of Dresscode Malware Found on Google Play Store, Say Researchers." ZDNet. https://www.zdnet.com/article/over-400-instances-of-dresscode-malware-found-on-google-play-store-say-researchers/.
- Vijayan, Jai. 2020. "'Unkillable' Android Malware App Continues to Infect Devices Worldwide." https://www.darkreading.com/mobile/unkillable-android-malware-app-continues-to-infect-devices-worldwide/d/d-id/1337519.
- Wong, Wylie. 2018. "New Malware-as-a-Service Threat Targets Android Phones." https://securityintelligence.com/news/new-malware-as-a-service-threat-targets-android-phones/.
- Google. 2020. "Security Risks with Modified (Rooted) Android Versions." https://support.google.com/accounts/answer/9211246?hl=en.
- Chuluundorj, Zorigtbaatar. 2019. "Augmenting Network Flows with User Interface Context to Inform Access Control Decisions." Master's thesis, Worcester Polytechnic Institute. https://digitalcommons.wpi.edu/etd-theses/1331.
- Demetriou, Soteris, Nan Zhang, Yeonjoon Lee, XiaoFeng Wang, Carl A Gunter, Xiaoyong Zhou, and Michael Grace. 2017. "HanGuard: SDN-Driven Protection of Smart Home WiFi Devices from Malicious Mobile Apps." In Proceedings of the 10th ACM Conference on Security and Privacy in Wireless and Mobile Networks, 122–33.
- Yang, Zhemin, Min Yang, Yuan Zhang, Guofei Gu, Peng Ning, and X Sean Wang. 2013. "AppIntent: Analyzing Sensitive Data Transmission in Android for Privacy Leakage Detection." In Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, 1043–54.
- Kwon, Jonghoon, Jehyun Lee, and Heejo Lee. 2011. "Hidden Bot Detection by Tracing Non-Human Generated Traffic at the Zombie Host." In International Conference on Information Security Practice and Experience, 343–61. Springer.